Jnk (Diskussion | Beiträge) |
|||
| Zeile 5: | Zeile 5: | ||
}} | }} | ||
| − | Zoom meetings are TLS encrypted (like https). This secures the conference against third parties like hackers. The campus license of the university Paderborn is provided by a company located in Germany ( | + | Zoom meetings are TLS encrypted (like https). This secures the conference against third parties like hackers. The campus license of the university Paderborn is provided by a company located in Germany (Deutsche Telekom). TLS encryption can’t secure the conversations against access of zoom or C4V. Both parties assure they don’t access the conversations but this can’t be guaranteed. |
| − | + | <br> | |
Confidential conversations can be held by using the end-to-end-encryption (E2EE). With this option, neither zoom nor C4V can access the content of the video conference. While using the end-to-end-encryption, not all zoom features are available. For end-to-end encrypted meetings, the Zoom client must be used. Joining the conference via browser is not possible. | Confidential conversations can be held by using the end-to-end-encryption (E2EE). With this option, neither zoom nor C4V can access the content of the video conference. While using the end-to-end-encryption, not all zoom features are available. For end-to-end encrypted meetings, the Zoom client must be used. Joining the conference via browser is not possible. | ||
| + | <br> | ||
| − | Additional to the content of the conversations, zoom is gathering metadata. Examples are the IP address of the participants, device and hardware information, browser configuration, name and description of the meeting, date, time, duration of the meeting and number of participants. These information are available for | + | Additional to the content of the conversations, zoom is gathering metadata. Examples are the IP address of the participants, device and hardware information, browser configuration, name and description of the meeting, date, time, duration of the meeting and number of participants. These information are available for Zoom and the Deutsche Telekom, even when the end-to-end-encryption is used. This information can be transferred to zoom USA for problem diagnosis and enhanced user experience. In case of privacy, gathering metadata must be seen critical. |
| − | + | <br> | |
| − | |||
For conferences with confidential information like job interviews, appraisal interviews, appeal hearings, senate and chair conferences Zoom can only be used after a consideration of data protection laws by the host and only with activated end-to-end encryption. | For conferences with confidential information like job interviews, appraisal interviews, appeal hearings, senate and chair conferences Zoom can only be used after a consideration of data protection laws by the host and only with activated end-to-end encryption. | ||
Version vom 24. November 2023, 12:27 Uhr
Zoom meetings are TLS encrypted (like https). This secures the conference against third parties like hackers. The campus license of the university Paderborn is provided by a company located in Germany (Deutsche Telekom). TLS encryption can’t secure the conversations against access of zoom or C4V. Both parties assure they don’t access the conversations but this can’t be guaranteed.
Confidential conversations can be held by using the end-to-end-encryption (E2EE). With this option, neither zoom nor C4V can access the content of the video conference. While using the end-to-end-encryption, not all zoom features are available. For end-to-end encrypted meetings, the Zoom client must be used. Joining the conference via browser is not possible.
Additional to the content of the conversations, zoom is gathering metadata. Examples are the IP address of the participants, device and hardware information, browser configuration, name and description of the meeting, date, time, duration of the meeting and number of participants. These information are available for Zoom and the Deutsche Telekom, even when the end-to-end-encryption is used. This information can be transferred to zoom USA for problem diagnosis and enhanced user experience. In case of privacy, gathering metadata must be seen critical.
For conferences with confidential information like job interviews, appraisal interviews, appeal hearings, senate and chair conferences Zoom can only be used after a consideration of data protection laws by the host and only with activated end-to-end encryption.
For courses, lectures, seminars, conventions and public events, zoom normally can be used in default settings.
Requirements for E2EE[Bearbeiten | Quelltext bearbeiten]
The participants need to have the zoom client in version 5.4.0 or newer installed. Joining via browser is not possible. (Feb 2021)
Restrictions[Bearbeiten | Quelltext bearbeiten]
With activated end-to-end-encryption, the following features are not available: (February 2021)
- Polling
- Breakout Rooms
- Cloud recording
- Join before host
- Live transcription
- Live Streaming
- Join by phone
The following features are only available by using the Zoom Client in Version 5.5.0 or higher:
- Meeting reactions (like "raise hand")
- 1:1 private chats
Joining end-to-end-encrypted meetings via browser is not possible.
Encryption[Bearbeiten | Quelltext bearbeiten]
Activate end-to-end-encryption[Bearbeiten | Quelltext bearbeiten]
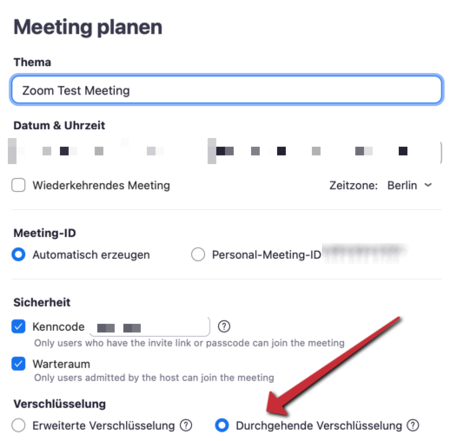
Use the following settings to activate end-to-end-encryption.
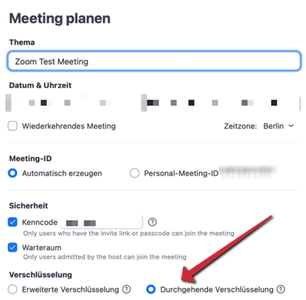
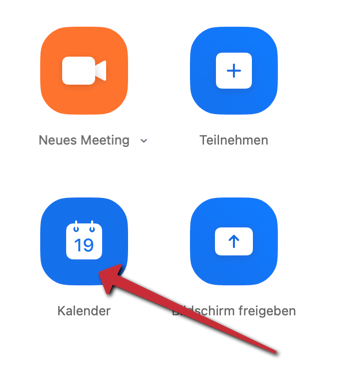
- Use the Calendar to create a new Zoom meeting.
- Activate end-to-end encryption.
End-to-end encryption as default[Bearbeiten | Quelltext bearbeiten]
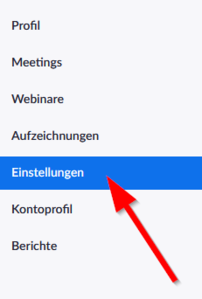
You can set end-to-end-encryption as the default setting for Zoom meetings. Open the Zoom account in your browser.
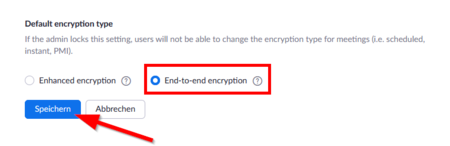
- Click on „Settings“.
- Click on „End-to-end encryption“ as default.
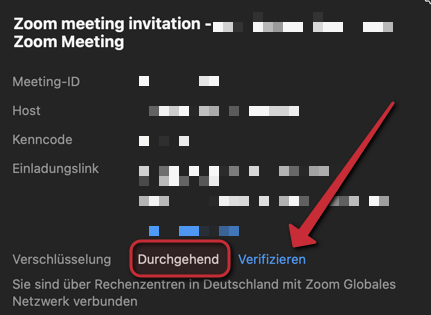
Verify encryption[Bearbeiten | Quelltext bearbeiten]
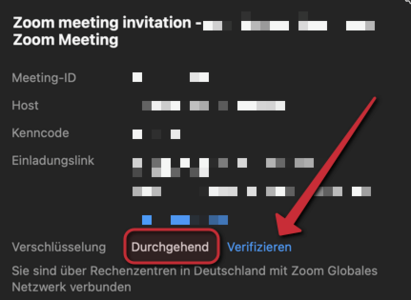
In the meeting, the symbol in the top left hand corner shows you, which encryption is active.
| Check on green shield. Only TLS encrypted. For non confidential meetings. | |
| Lock on green shield. End-to-end-encryption active. For confidential meetings. |
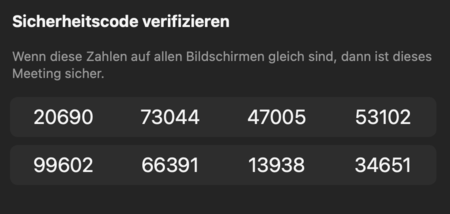
Compare the security codes, to check if the meeting is secure. Click on the green Symbol.
See also[Bearbeiten | Quelltext bearbeiten]
- Zoom - All articles about Zoom
- Zoom-Datenschutzerklärung & Zoom-Nutzungserklärung
- Alle Artikel zum Thema Videokonferenzen - Auch Alternativen zu Zoom