This article explains the options available when using file encryption. It focuses on the storage of data at network locations and how to protect the data stored there from unauthorized access and manipulation.
Why should I use file encryption?[Bearbeiten | Quelltext bearbeiten]
When working with personal data, it can quickly happen that these data have a special need for protection. Since remote data storage devices do not provide protection of confidentiality (access by third parties) or integrity (manipulation of data), it is necessary to additionally secure data worthy of protection.
Which data is particularly worthy of protection is usually only known in the event of damage, so a special duty of care applies when storing data with external services.
The official Sciebo user regulations of the University of Paderborn
link to the user regulations is missing |
provide an assessment of which data must be encrypted or may not be stored in Sciebo at all. You can use this user policy as a guide for file exchange over the network until a basic user policy for other services, such as network storage, is in place.
Use encryption programs[Bearbeiten | Quelltext bearbeiten]
An encryption program simplifies your work with encrypted files. Usually, this involves generating file(s) that are stored encrypted and protected against manipulation by a cryptographic hash procedure. After entering the correct password, these files are decrypted, checked and then made available as an additional drive in the operating system.
It is important to choose the right program, as the programs often want to achieve different protection goals. These are often not immediately apparent to the user. There are programs that only encrypt but do not protect against manipulation and also programs that only protect against manipulation but do not offer confidentiality.
Arrangements[Bearbeiten | Quelltext bearbeiten]
Sciebo[Bearbeiten | Quelltext bearbeiten]
To use encryption conveniently, you should always install the Sciebo synchronization client. This allows you to work comfortably with Sciebo and ensures that your data is always kept up to date.
Installation instructions can be found on the official Sciebo help pages: https://www.sciebo.de/anleitung/desktop.html
Network storage[Bearbeiten | Quelltext bearbeiten]
To be able to work comfortably with the network storage, you should first mount the network storage.
You can find instructions here in the help wiki: Netzlaufwerk einbinden
Programs[Bearbeiten | Quelltext bearbeiten]
Below is a selection of programs that can be used to encrypt files in a network.
Cryptomator[Bearbeiten | Quelltext bearbeiten]
Cryptomator is an open source tool that can be downloaded for free. There are versions for all common platforms and smartphones.
You can find the latest version of Cryptomator in the download area of https://cryptomator.org/
Installation and Setup (Windows)[Bearbeiten | Quelltext bearbeiten]
Sciebo specific configuration[Bearbeiten | Quelltext bearbeiten]
This first step is optional. It is only meant to help you find your personal Sciebo folder easily. If you have no problems with this, you can skip it.
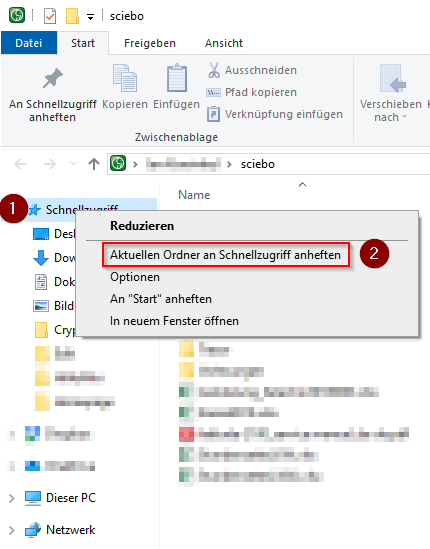
- Right click on the Sciebo symbol at the bottom right
- If the Sciebo symbol is not displayed, it may be hidden behind the up arrow
- click on "Folder >>sciebo<< open"
- Now you will see your personal sciebo folder
- Right click on the lettering "DeepL Access" on the left-hand side
- Now pin the folder in the context menu
General configuration[Bearbeiten | Quelltext bearbeiten]
- Download the Cryptomator program
- Install Cryptomator. Here you can use the default settings.
- Some antivirus programs block the installation of Cryptomator with a warning message. As long as you have downloaded the installation file from the above link, you can ignore this.
- After installation Cryptomator must be set up
- To encrypt files with Cryptomator, we need an encrypted drive These are called vaults by Cryptomator.
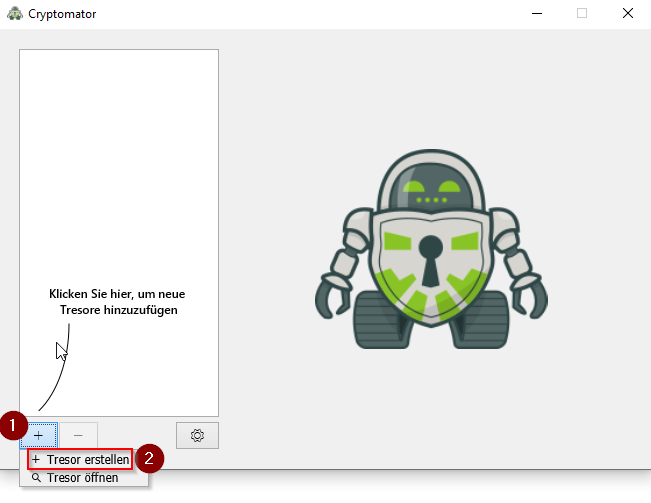
- On the left side you can see the already existing vaults. The list is empty, so we start by creating a new vault.
- With a click on the + symbol you open the options
- Click on "Create safe"
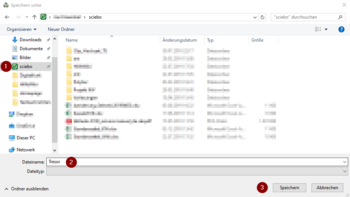
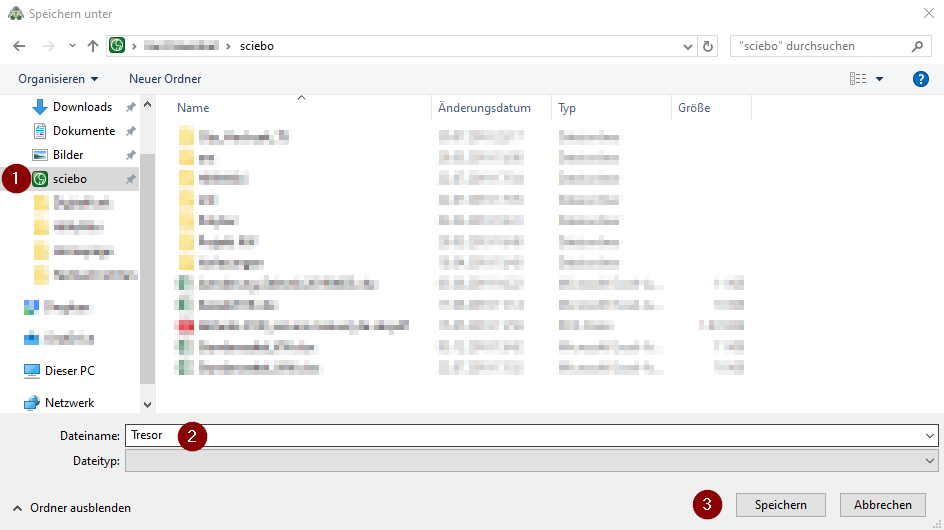
- As storage location we select the "sciebo" folder or any other folder for example on the network storage. If you followed the sciebo instructions, you will find it directly in the DeepL access
- As file name we assign an unambiguous term, here as example "safe"
- With a click on "Save" we continue
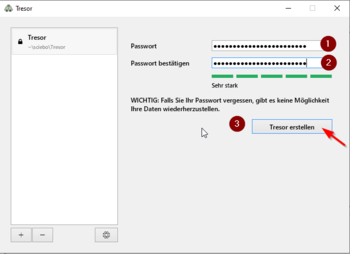
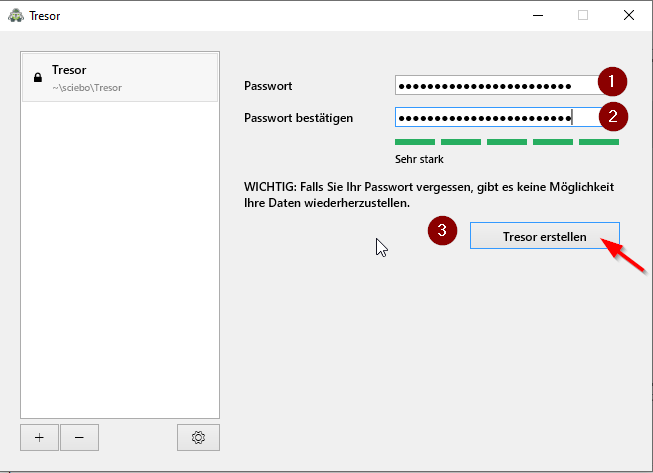
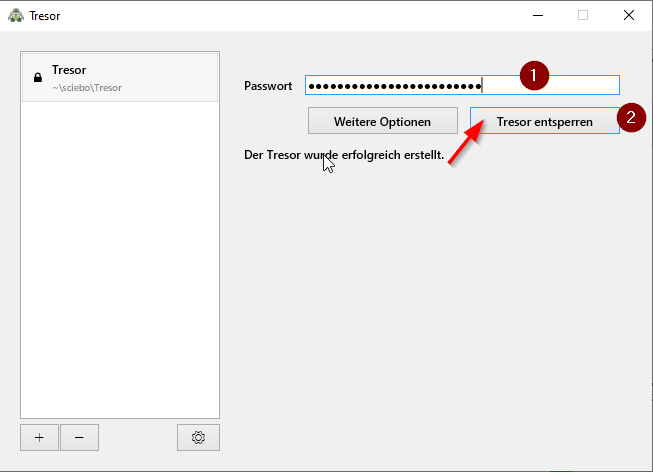
- Now we assign a password for our encrypted drive
- The password should have at least 10 characters and consist of uppercase letters, lowercase letters, numbers and special characters
- Cryptomator informs you directly about how secure your chosen password is
- Repeat the password and complete the step with "Create safe
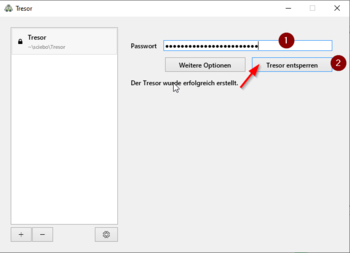
- We have now created a vault and already encrypted it with Cryptomator
- To use it, we must first unlock it
- Enter the password for the safe and then click on "Unlock safe".
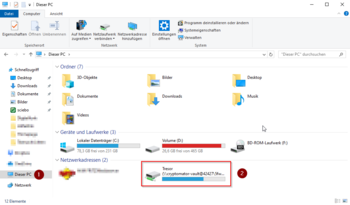
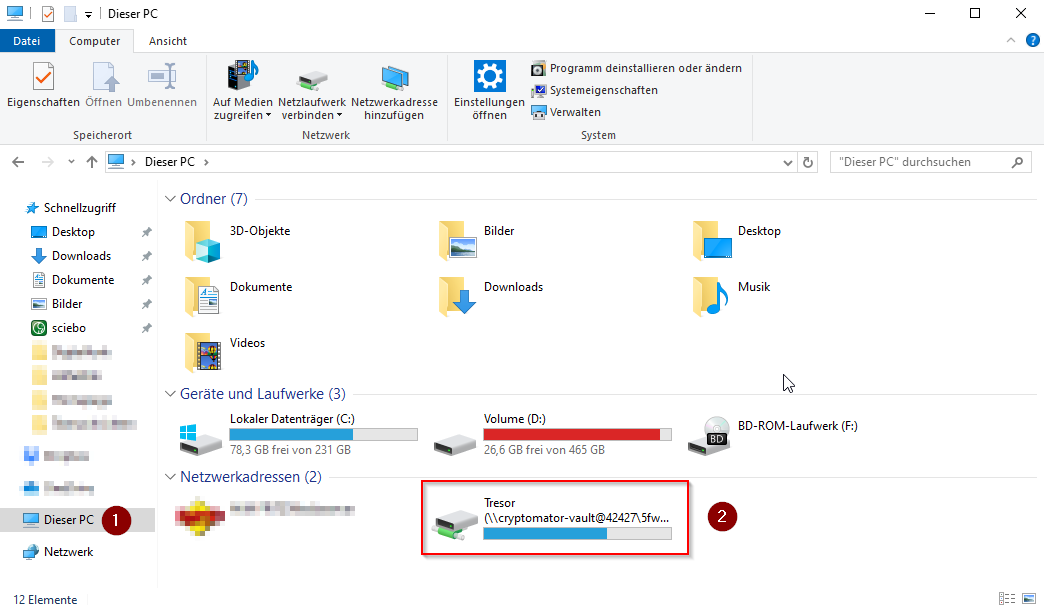
- To use our vault, we call up Windows Explorer
- Click on "This PC" on the left side
- Under the network addresses you will now find a new network drive, which can be opened with a double click
- All files moved here are now automatically encrypted
Veracrypt[Bearbeiten | Quelltext bearbeiten]
With Veracrypt different types of encryption can be implemented. However, the focus of this article is on creating a secure container file that can be synchronized with Sciebo. The use of Veracrypt is rather aimed at experienced users, as it offers many setting options that are not relevant for the standard user.
You can find the latest version of Veracrypt in the download area of https://www.veracrypt.fr/
Installation and Setup (Windows)[Bearbeiten | Quelltext bearbeiten]
For instructions on how to create an encrypted container with Veracrypt, visit the VeraCrypt web pages: Veracrypt Beginner's Tutorial
Encryption capabilities of Office programs[Bearbeiten | Quelltext bearbeiten]
Single documents[Bearbeiten | Quelltext bearbeiten]
For the distribution it is also possible to protect the files themselves. For this purpose, the individual programs often offer the possibility to secure the files with a password. For this purpose we ask you to use the help pages of the respective program used, as we cannot list and compare all programs here. We also cannot give any guarantee about the quality and type of encryption. Please consider this list only as an indication.
Common programs that can encrypt individual documents:
- Adobe Reader, FoxIt PDF
- Microsoft Office (Word, PowerPoint, Excel, ...)
- LibreOffice, OpenOffice
Multiple documents[Bearbeiten | Quelltext bearbeiten]
If you want to share several files encrypted at once, common compression programs (7-Zip, WinRAR, ...) can set passwords on file archives. But please keep in mind that a recipient will unpack the files and thus store unencrypted files locally on his system. This kind of file sharing is also not recommended for collaborative work, because the documents have to be protected again and again, which consumes a lot of time and data that other solutions do more elegantly.
Important[Bearbeiten | Quelltext bearbeiten]
Never send unencrypted e-mails with passwords! Please send the passwords in another way or use encrypted communication.
For Sciebo, it is also important to ensure that at no time are the unencrypted files stored in the synchronization folder, as these can be synchronized immediately and theoretically restored even after deletion. Please check if the encryption works correctly by downloading and opening the encrypted files e.g. via the Sciebo website. If the correct file content is displayed, there is a configuration error.
Furthermore, you must be aware that if you lose your password, the files are irretrievably deleted. There is no service provider who can restore these files.
External help pages[Bearbeiten | Quelltext bearbeiten]
The following pages contain general assistance for the individual programs. These pages are not checked for up-to-dateness and should only be a first point of contact for further problems.
https://www.uni-due.de/zim/services/sciebo/verschluesselung.php